Preventing Malware with Microsoft Defender for Endpoint
Introduction
In my previous post I looked at some barebones configuration
to get started with MDE, now let’s look at locking down your environment.
MDE includes many settings to minimise the overall attack
surface of your Windows devices, one of these features is the ability to apply
Attack Surface Reduction (ASR) rules. In a nutshell they prevent malware
infection by blocking certain software behaviours, like:
- Scripts and executables attempting to download or run files
- Running suspicious scripts
- Behaviours outside of the normal day-to-day operation
Microsoft provide Security Baselines for Windows and
Defender which include ASR rules, but the default setting for these can be a little on the overzealous side and from experience can impede end users’ ability to work,
so tuning these to suit your environment is important.
Before implementing a block rule across your Windows estate, ensure you’ve run the rule in audit mode to verify normal end user operations won’t be impacted. Microsoft’s recommendation is as follows:
If issues are discovered during the testing phase, instead
of completely disabling a rule it may be possible to simply exclude an
executable from ASR rules. This obviously comes with risk, but worth exploring
if the need arises. More information on this can be found here
Configuration
The settings below are the result of implementing ASR rules
into various environments and discovering which ones are too intrusive. These
may work for most environments, but make sure to test, test, test.
- Block untrusted and unsigned processes that run from USB Block
- Block Adobe Reader from creating child processes Block
- Block executable content from email client and webmail Block
- Block JavaScript or VBScript from launching downloaded executable content Block
- Block persistence through WMI event subscription Block
- Block credential stealing from the Windows local security authority subsystem (lsass.exe) Block
- Block Office applications from creating executable content Block
- Block Office applications from injecting code into other processes Audit
- Block Win32 API calls from Office macros Audit
- Block all Office applications from creating child processes Audit
- Block execution of potentially obfuscated scripts Audit
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion Audit
- Use advanced protection against ransomware Audit
- Block process creations originating from PSExec and WMI commands Audit
- Block Office communication applications from creating child processes Audit
- Use advanced protection against ransomware Audit
In my next post, I’ll be looking at further settings to lock
down your Windows environment.
Laying the foundations in Microsoft Defender for Endpoint
Introduction
Create Device Groups
- Role based access control (RBAC)
- Configuring auto-remediation settings
- Filtering devices during remediation
- Configuring alert levels
Configure RBAC
Set Up Vulnerability Notifications
- New vulnerability found (including zero-day vulnerability)
- Exploit was verified
- New public exploit
- Exploit added to an exploit kit
Conclusion
Onboarding devices to Microsoft Defender for Endpoint with Intune
Introduction
Defender for Endpoint (Formerly Defender ATP) is Microsoft’s enterprise grade endpoint protection solution which provides prevention, detection, investigation and response to advanced threats. I regularly work with customers who already use Defender anti-virus and want to dip their toes into the enhanced capabilities of Defender for Endpoint (MDE).
What are the steps to onboard a device already being managed by Microsoft Endpoint Manager?
Prerequisites
Firstly, obtain licensing. I recommend Microsoft Defender for Endpoint Plan 2.
Identify a Windows device or several devices for the test. These need to be active devices in MEM.
An Azure AD security group containing the devices/users in scope for the test needs to be created.
Browse to the Microsoft 365 Defender web page, if Defender hasn’t been previously enabled, click through the ‘first run’ options to choose region, data retention etc.
Then enable “Microsoft Intune Connection” under Settings -> Endpoints -> Advanced features. This connection may take up to 24 hours to establish.
Configuration
Now we’re ready to target a configuration profile to onboard a device with MDE.
To create the configuration profile within the MEM admin center, browse to Endpoint security -> Endpoint detection and response and create a new policy.
The onboarding blob is automatically created by the connection between MEM and MDE, so no further configuration is required in the profile here.
Once the profile is created, assign to the security group containing users/devices in scope for the test.
If all has gone well, the device will appear in the “Devices” section of the Microsoft 365 Defender page.
Testing
Once the configuration profile has been received by the device and telemetry has been sent to MDE, you’ll begin to see data in Microsoft 365 Defender webpage.
To test the connection with MDE, we can trigger a test alert by running the command line shown in the Onboarding section of Settings -> Endpoints.
A great way to verify MDE is working is to disable automated patching on the test device (exclude from Windows Update Rings). This will eventually result in the device to become behind in patching levels and further data will appear in Microsoft 365 Defender about known vulnerabilities.
Conclusion
Hopefully this post has provided some quick steps to onboard a test device or devices into Microsoft Defender for Endpoint ready for demonstration of further features.
I will be publishing more posts which demonstrate some of the excellent features MDE has to offer.
Next Post - Laying the foundations in Microsoft Defender for Endpoint
Onboarding remote devices with Microsoft ConfigMgr or Intune
Introduction
The end user computing landscape has drastically changed over the last few years due to the drive towards remote working, and with this comes a need to rethink device management.
For Windows devices, ConfigMgr or Intune have been the go-to solutions from Microsoft under the Endpoint Manager umbrella. The combination of the two platforms brings a truly comprehensive approach to managing a Windows estate.
Since the adoption of remote working, I’ve regularly been asked about how to onboard or migrate VPN connected, Active Directory domain joined Windows devices into Microsoft Endpoint Manager with the least amount of IT staff intervention. In this post, I’ll look a couple of scenarios I’ve encountered and how I dealt with each one with some high-level bullet pointed steps. It is assumed that ConfigMgr and Intune have already been configured up to the point of being functional.
Disclaimer: This is not a how-to guide, it's more about explaining the options available. I provide links for further reading.
Scenario 1
Requirement:
VPN connected clients need to be managed with ConfigMgr.
Scenario:
o
Devices never return to office
o
AD domain joined only
o No ConfigMgr Client installed
Solution:
1.
Create GPO with ConfigMgr site assignment and client
deployment settings (Excellent how to guide here)
2.
Add software package installation to GPO using ccmsetup.msi hosted on a contactable file share
3.
Link GPO to OU containing target devices
Explanation:
With a few basic configuration changes, it’s possible to
take a large number of remotely connected devices from a position of no
management to being fully managed with ConfigMgr.
Scenario 2
Requirement:
Co-management with a CMG is needed to manage devices.
Scenario:
o
AD domain joined only
o
ConfigMgr Client installed
o No Cloud Management Gateway
Solution:
1.
Configure Azure AD Connect for Hybrid AAD join (More details)
2.
Manually create a Group Policy to apply the
client-side SCP registry entry (More details)
3.
Configure Intune Automatic Enrollment and
Co-management settings in ConfigMgr (More details)
4.
Provision a Cloud Management Gateway (More details)
Explanation:
A more modern approach to device management can be achieved with
co-management. Once these configuration changes have been implemented, Intune
could be used to manage workloads such as Software Updates or Compliance while
ConfigMgr remains in play for other tasks such as App deployment and inventory.
A CMG will allow ConfigMgr to continue managing devices even when they’re
internet-based (out of the office and disconnected from VPN).
Of course, once the devices are in this co-managed state, there is scope to transition away from ConfigMgr and aim for fully modern-management.
ConfigMgr CMG "Failed to list keys for storage service"
When provisioning a vm scale set ConfigMgr Cloud Management Gateway and the following errors are shown in the CloudMgr.log:
ERROR: TaskManager: Task [AnalyticsCollectionTask: Service xxxxxxxxxx] has failed. Exception Hyak.Common.CloudException, Failed to start deployment slot.
ERROR: Resource Manager - Failed to list keys for storage service xxxxxxxxxx with status code NotFound. Check [Monitor/Activity log] on Azure Portal for more information
Ensure the Azure ConfigMgr Server Application has been granted at least contributor rights in the Azure subscription being used.
ConfigMgr CMG provisioning error "Failed to finish deployment"
When deploying a ConfigMgr Cloud Management Gateway to Azure using VM scale sets and you receive the following error in CloudMgr.log:
ERROR: Resource Manager - Deployment operation details: {"value":[{"id":"/subscriptions/xxxxxxxxxxxx/resourceGroups/xxxxxxxx/providers/Microsoft.Resources/deployments/CreateKeyVaultd7fa35f7-7f9a-4a49-b780-2e3d267f29a3/operations/4B42A1CC456C4E8A","operationId":"4B42A1CC456C4E8A","properties":{"provisioningOperation":"Create","provisioningState":"Failed","timestamp":"2022-08-24T09:29:33.5616488Z","duration":"PT0.2383212S","trackingId":"f183ade1-5a45-4cd4-ab63-b3ca7801f48a","statusCode":"Conflict","statusMessage":{"error":{"code":"MissingSubscriptionRegistration","message":"The subscription is not registered to use namespace 'Microsoft.KeyVault'. See https://aka.ms/rps-not-found for how to register subscriptions.","details":[{"code":"MissingSubscriptionRegistration","target":"Microsoft.KeyVault","message":"The subscription is not registered to use namespace 'Microsoft.KeyVault'. See https://aka.ms/rps-not-found for how to register subscriptions."}]}},"targetResource":{"id":"/subscriptions/6f6636c7-bca4-43df-af17-190bcc9992d5/resourceGroups/xxxxxxxxxx/providers/Microsoft.KeyVault/vaults/xxxxxxxxxx","resourceType":"Microsoft.KeyVault/vaults","resourceName":"xxxxxxxxxxxxxx"}}}]}
You'll need to log on to the Azure portal and perform the following:
1. Find the Azure subscription being used for the CMG and select it
2. Select "Resource Providers" on the left hand side
3. Register "Microsoft.KeyVault", "Microsoft.Compute" & "Microsoft.Network"
4. Within a few seconds the Resource Providers will have been registered.
5. Retry CMG provisioning from ConfigMgr console (delete previous attempt and re-provision.)
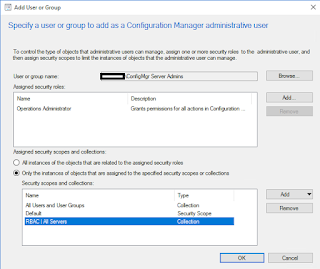
Implementing Role Based Access Control (RBAC) with ConfigMgr Part 1 - Basic Security Roles
Part 2 - Implementing RBAC with ConfigMgr - Security Scopes [COMING SOON]
Introduction
Scenario
- ConfigMgr admins - Responsible for ConfigMgr operations, day to day tasks require full control of all objects.
- Server admins - Members of the server team responsible for maintaining Windows servers.
- Desktop admins - Members of the desktop team responsible for maintaining Windows desktops.
- Service desk admins - Support the end user environment and require limited functionality within ConfigMgr.
- Security auditors - Responsible for auditing organisational platforms, read only to all objects is sufficient.
Collection Limiting
Server admins - Scoped to "Windows Servers" device collection
Desktop admins - Scoped to "Windows Desktops" device collection
The following custom device collections have been created with the limiting collection in brackets:
Windows 2016 Servers (Windows Servers)
*Deploy VMWare Tools (All Desktop and Server Clients)
Windows 10 Desktops (Windows Desktops)
*Deploy O365 ProPlus (All Desktop and Server Clients)
Neither a server admin or a desktop admin would be able to see the device collections highlighted with *.
To rectify this, simply change the limiting collection on both highlighted device collections. This can either directly reference the scoping collection or a "child" device collection. E.g.:
Windows 2016 Servers (Windows Servers)
Deploy VMWare Tools (Windows Servers)
Windows 10 Desktops (Windows Desktops)
Deploy O365 ProPlus (Windows Desktops)
You'll need to review the device collections in your environment and plan ahead for this.
Implement
1. Create device collection hierarchy
2. Create Active Directory security groups
3. Add security groups to ConfigMgr security
4. Update limiting collections
Validate
Conclusion
Deploy a ConfigMgr Secondary Site with SCCM 1906
Introduction
- The WAN link back to the primary site server is slow or unreliable
- Content needs to be distributed at specific times of the day
Overview
Prerequisites
2. Select Computer Management
3. Open Local Users and Groups
4. Open Groups
5. Open the Administrators group
6. Click Add
7. Click Object Types, tick Computers and click OK
Create no_sms_on_drive.sms file on all volumes except the Configuration Manager content volume.
Install Windows Features and Roles
Install and Configure WSUS
Install Secondary Site
Install Software Update Point
1. Navigate to Administration -> Site Configuration -> Servers and Site System Roles2. Right click on the secondary site server and select Add Site System Roles
3. On the role selection screen, select Software Update Point and next
Provision and Build Windows VM's in a Hyper-V Lab Environment Using PowerShell and ConfigMgr
Background
Hyper-V Provisioning
ConfigMgr OSDComputerName
SCCM Cloud Management Gateway Error: Task [CreateDeployment for service (CMG NAME)] has failed
CloudMgr.log
ERROR: Resource Manager - Failed to finish deployment. Check [Monitor/Activity log] on Azure Portal for more information
ERROR: Resource Manager - Deployment operation details: {"value":[{"id":"/subscriptions/e672f87f-12ed-4c34-879b-8181e3f0e994/resourceGroups/####/providers/Microsoft.Resources/deployments/CreateCloudServiceb929f43b-abac-412b-aa3f-2920883c39d3/operations/F5DF9DE74E0F058F","operationId":"F5DF9DE74E0F058F","properties":{"provisioningOperation":"Create","provisioningState":"Failed","timestamp":"2019-01-22T08:05:33.5763846Z","duration":"PT3.789856S","trackingId":"e2a743a1-e659-44d5-bce8-22baf66e4ed4","statusCode":"Conflict","statusMessage":{"error":{"code":"MissingSubscriptionRegistration","message":"The subscription is not registered to use namespace 'Microsoft.ClassicCompute'. See https://aka.ms/rps-not-found for how to register subscriptions.","details":[{"code":"MissingSubscriptionRegistration","target":"Microsoft.ClassicCompute","message":"The subscription is not registered to use namespace 'Microsoft.ClassicCompute'. See https://aka.ms/rps-not-found for how to register subscriptions."}]}},"targetResource":{"id":"/subscriptions/e672f87f-12ed-4c34-879b-8181e3f0e994/resourceGroups/####/providers/Microsoft.ClassicCompute/domainNames/####","resourceType":"Microsoft.ClassicCompute/domainNames","resourceName":"####"}}}]}
ERROR: Exception occured for service ###### : Hyak.Common.CloudException: Failed to finish deployment~~ at Microsoft.ConfigurationManager.AzureManagement.ResourceManager.StartAndMonitorDeployment(String resourceGroupName, String deploymentName, Deployment deploymentProp, Int32 secondsToWait, Int32 timeoutInMinutes)~~ at Microsoft.ConfigurationManager.AzureManagement.ResourceManager.CreateCloudService(String resourceGroupName, String cloudServiceName, String location, Int32 timeoutInMinutes)~~ at Microsoft.ConfigurationManager.CloudServicesManager.CreateDeploymentTask.Start(Object taskState).
The key piece of information is hidden in the middle and reads: The subscription is not registered to use namespace 'Microsoft.ClassicCompute'
This quite clearly states the problem, I obviously need to register the resource provider 'Microsoft.ClassicCompute' on the Azure subscription being used to provision the CMG.
The fix
To register a resource provider on the subscription, follow these steps:1. In the Azure portal, All Services > Subscriptions
2. Select the subscription being used
3. Click Resource Providers
4. Find Microsoft.ClassicCompute in the list of available resource providers and hit Register
After a minute or two you'll see the resource provider registered with the subscription (you may need to hit refresh).
After registration the cloud management gateway installed successfully.
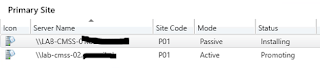
Promote Passive SCCM Site Server to Active
- In the SCCM console, navigate to Administration > Site Configuration > Sites
- Select site and switch to the Nodes tab
- Right Click the passive site server, click Promote to active, and Yes
- Refresh the console to view the current status.
- For more details, open Monitoring > Overview > Site Server Status and right click to Show Status
Install SCCM 1806 with HA Site Servers in a lab
This guide will walk you through installing a fresh SCCM 1806 environment and demonstrate the site server active/passive functionality. As you can see from the design below, only the SCCM site servers are highly available. In a production environment you'd host the site database on a SQL cluster or AOAG, and have multiple site systems hosting the SCCM client facing roles (MP, DP, SUP etc). This guide will not cover installing the SQL server.
Prerequisites and Requirements
- Configure a separate SQL Instance (HA in production).
- Create a network location for site content library, read/write granted to site servers.
- Both site servers need to be on same domain.
- SCCM needs to be a standalone site.
- Both servers must use the same remote database.
- Both servers need sysadmin permissions on the site database SQL instance.
- Both servers must be local admin on each other.
- Both servers much be local admin on SQL server hosting site database.
Step-by-Step
1. Create SCCM user accounts
2. Extend Active Directory schema
3. Create System Management container
- Log on as an account that has the Create All Child Objects permission on the System container in Active Directory Domain Services.
- Run ADSI Edit, and connect to the domain in which the site server resides.
- Expand Domain <computer fully qualified domain name>, expand <distinguished name>, right-click CN=System, click New, and then click Object.
- In the Create Object dialog box, select Container, and then click Next.
- In the Value box, type System Management, and then click Next.
- Click Finish.
- Grant the computer account of each SCCM site system full control over the container and all descendant objects.
4. Install all prerequisites on each of the servers.
5. Install the Windows ADK on each site server.
- Download and install the Windows 10 ADK from:
- Initiate the installation of SCCM on the active site server (LAB-CMSS-01)
- Enter product key
- Download installation prerequisite content
- Configure site settings
- Do not install DP or MP roles at this stage
- Once complete, configure discovery methods (forest discovery with boundary creation at a minimum) and then create a boundary group for your domain.
7. Manage content library
- Within the SCCM console Administration > Site Configuration > Sites
- Select the site and click Manage Content Library in the ribbon bar.
- Enter the UNC path to the network share to host the content library
- Monitor the distmgr.log for errors.
- The new location needs to be a directory within a share
- If the move fails initially, use the ConfigMgr service manager to restart the SMS_DISTRIBUTION_MANAGER component once you've resolved errors.
8. Install the passive site server.
- In the SCCM console Administration > Site Configuration > Sites
- Click Create Site System Server
- Enter the FQDN of the passive server and select the site.
- Select the role Site Server in passive mode
- Enter the path to source files, it's recommended to use the cd.latest folder in the site share.
- Enter the installation folder on the destination server.
- Monitor the installation progress in Monitoring > Site Server Status
- Click Show Status for more detail.
9. Install additional SMS Provider
- On the active site server, load the SCCM setup wizard from media, or click Uninstall/Change when selecting SCCM in Control Panel > Program and Features
- Select Perform Site Maintenance or Reset This Site
- Choose Modify SMS Provider Configuration
- Choose Add a new SMS Provider and enter the FQDN of the passive site server.
- Complete setup wizard.
10. Install site system
- Navigate to Administration > Site Configuration > Servers and Site System Roles
- Click Create Site System Server
- Enter FQDN of site system and select site in drop down box
- Select Management Point and Distribution Point roles
- Complete the rest of the wizard with settings to meet your requirements.
Test site server promotion
About Me

- Tom Pearson
- Senior Consultant at CDW UK specialising in Microsoft workspace and cloud technologies.